Jared Kushner is currently taking a victory lap, crowin’ about his “Stealth Data Machine” that put Donald Trump over the top in the 2016 race. Let’s pry off the lid and peer into the inner-workings of this “Data Machine.”
The Signal in the Noise
Building on the data analysis by @Conspirator0 on Twitter, Tea Pain has stumbled onto a possible “signal in the noise” that opens a window into the data-swappin’ shenanigans going on between Trump Tower, Spectrum Health and Russia’s Alfa Bank during the election.
Spectrum Health, owned by Michigan’s powerful Devos family, attempted to explain the IP activity as “Voice over IP traffic”, whereas Alfa Bank offered an even more exotic explanation that “hackers attempted to make it look like we contacted Trump Tower.”
The data traffic, when analyzed, tells a very different story, a story of automated, orchestrated data sharing among multiple sites for a strategic end.
Tea Pain originally dismissed this story as a possible red-herring. With the Russia craze at a fever pitch, this activity could be explained by what Tea’s daddy used to say, “When you got a new hammer, everything looks like a nail.” But when Tea Pain saw the data patterns analyzed by Conspiritor0, he knew he’d spotted something mighty familiar: Database Replication. Put a pin in that, more on that later.
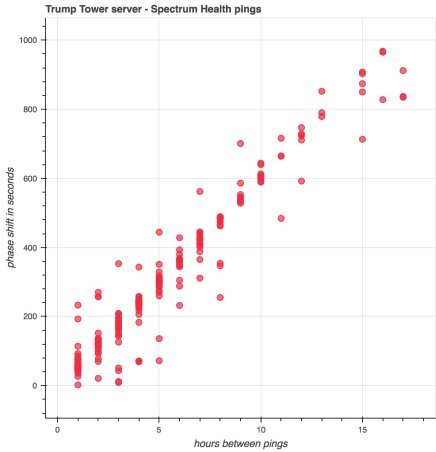
At first, data analysts were puzzled by what appeared to be random activity with no apparent pattern. Perhaps it was email activity? Maybe money transfers? But there were literally thousands of these IP “pings.”
Once the activity was charted, a pattern emerged. For example, a connection is made from Alfa Bank to Trump Tower, which may last anywhere from 1 minute to 15 minutes or more, followed by a longer “sleep” period. When averaged over months, these events charted an average time between connections to be 3660 seconds, or 1 hour and 1 minute. Whatever was running, it would hook up, transfer data for a few minutes, then go to sleep for an hour.
This was the clue that led Tea Pain to formulate a much clearer working model to explain what we were all seeing: SQL Server Database Replication between multiple sites.

What Is Database Replication?
Database Replication is a rather simple concept. When you have a database with millions of records representing hundreds of gigabytes of data, and you would like to keep a copy of that database housed in 2 or more locations, it makes no sense to continually copy the entire database from point A to point B every time a change is made, so you “replicate” it.
This allows only the changes made to be sent from one database to another. This is accomplished by a process that runs on timely intervals, usually an hour, that wakes up and checks the changes made since the last hour and broadcasts those changes to the other database. The other database, in turn, check for its changes and broadcasts them in the other direction. Voila! Both databases are identical!
So what does the data traffic patterns suggest? Check out the chart below. Behold, Kushner’s “Stealth Data Machine.”

The white box illustrates the scope of data we can now observe. The bulk of the replication took place between Trump Tower and Alfa Bank, while smaller amounts of data were transferred between Trump Tower and Spectrum Health. If, for example, Trump Tower talked to Alfa Bank for 10 minutes, the next Spectrum-Trump Tower connection might last only one minute, indicating data replicated from Trump Tower to the Devos health care empire was being filtered, perhaps by “WHERE StateCode=’MI'” for example. But when changes were made at Spectrum, things looked very different.

Conspiritor0 noted that when Spectrum connected to Trump Tower, Trump Tower’s next connect time was significantly longer, indicating Spectrum had modified a large chunk of records that had to be synced to Trump Tower, then pushed on to Alfa Bank. This detail was important in identifying that replication was in use. In this scenario, Trump Tower was functioning as a center-point, a data distribution center if you will.
We don’t know what was in these data packets; that info is beyond our purview at this time, but ask yourself a simple question and you find your answer: “What do Trump Tower, the Devos Family and the Russians all have in common? A desire for Donald Trump to be President of the United States.
Tea Pain’s working theory is that Russia created a voter targeting database with information gleaned from hacked DNC data rolls and other data rolls “acquired” from other states to feed this growing contact database. That database originated at Russian Intelligence which was in turn replicated to Russia’s Alfa Bank. This is where the “data laundering” takes place, Alfa Bank is the pivot point where the FSB’s data fingerprints are wiped clean. Ironically Russia launders its data at the same place it launders its money.
At Trump Tower, more data could merged into this system using various legal sources as well. Spectrum Health could also add value to the data by matching names and addresses in their extensive healthcare databases to harvest email addresses and phone numbers to flesh out this list. All these changes would be promptly replicated back to Russia in a matter of hours.
Once back in the hands of Russian Intelligence, this massaged data could be programmatically matched up with social media handles to create a micro-targeted “hit list” for the thousand Russian trolls employed by Putin.
The Payoff
How is this a breakthrough? Now that we have identified the likely means of how this data was transferred, data analysts now have more precise points to search for to arrive at a complete reveal of the massive data collusion between Team Trump and America’s foremost adversary.
The “beauty” of this system is its simplicity. Here’s some bullet-points to sum up.
- No special software needed. SQL Server is used in most every major enterprise. Replication is a built-in tool. No mysterious hidden processes, viruses, malware, etc.
- Virtually undetectable. No one would blink an eye at data replication, a standard business practice.
- Could all be set up remotely with only VPN credentials and remote desktop access, information that is often shared via routine third-party data audits. No one inside Trump Tower or Spectrum’s IT department need be involved. One Russian Intelligence data operative could set this up in less than an hour at each location. No low-level “conspirators” needed.
- Value could be added to the data anywhere in the chain and it would promote back to Russian Intelligence within 2-3 hours.
- All data-transmission would be out in the open, mixed in with the daily flow of business.
- Even if found, the data would look benign, just names, addresses, phone numbers, email addresses, social media handles, etc. No financial information. It would look just like a contact lead database purchased from any data-mining merchant.
- Trump/Spectrum operatives and employees in the United States could interact with this list and have no clue the origins of the data were nefarious. This plain-sight approach was the key to its success.
Tea Pain… Your ‘user-friendly information layout was so incredibly easy to follow I think it’s right up Rachel Maddow’s alley. Have you reached out to TRMS to book a segment yet? If not, I’m SURE WE’LL ALL BE IN ATTENDANCE ! Pretty Please with a cherry on top? 🍒
LikeLiked by 14 people
Why don’t you stick up her ass and have her present it
LikeLiked by 1 person
Ignorant people like you say asinine things.
LikeLiked by 3 people
Now there’s civility for you!
LikeLike
touchee my Dearie
LikeLiked by 1 person
Anyone who doesn’t believe this article is an IDIOT and a sucker!!!
LikeLiked by 2 people
We will. Thank you very much.
LikeLike
Say hello to Vladamir!
LikeLike
Wow! Yes Spectrum Health bought up all the hospitals in a wide area of Michigan. Home base is Grand Rapids, where the De Voss family is located. This is very interesting indeed.
LikeLiked by 1 person
You rock patriot, keep up the good.
LikeLiked by 3 people
Thanks guys!!! I am SO sick of looking at his pumpkin head every day as he compounds his stupidity and ignorance with his irresponsible ignorance!
LikeLiked by 2 people
Humm. Diabolical. And Kushner tried or wanted to open a back channel to Russia from the WH.For all we know maybe he has? Talk about organized crime….RICO. I hope this is some of what Mueller and Team are working on.😈
LikeLiked by 2 people
Betsy”s server said to be run for her brother Eric? the black ops guy owns Blacksmithing that worked for Trump campaign and got her slot as he has a long history with Russia and other Intl dictator regimes. They have sold out America. Indict and Impeach now!
LikeLiked by 1 person
What if the DeVos/Spectrum Health Server was involved only as a Back-up Server in case the others were attacked or destroyed?
What if the Spectrum Health Server only provided targeting information for Michigan residents and facilitated just that end of the equation?
Don’t get me wrong, I believe all of this. There’s no real need to think these things have to be mutually exclusive, is there?
LikeLike
Review the billionaire far-right-wing DeVos family and Erik Prince connection before assuming an “innocent” role for Spectrum Health. After the election, an unqualified anti-public schools Betsy DeVos, sister to the head of the mercenaries-for-hire evangelically driven murderous (GW’s no-bid contractor) BLACKWATER group. Prince’s father was behind the AMWAY scam, and Erik Prince, who created Prince Group, attempted to convince Trump to let his mercenaries take over ($3000 per day per person) in Afghanistan. Follow the money and the lust(s) for power.
LikeLiked by 1 person
How is Betsy DeVos “unqualified”?
LikeLike
I think she did a show on this last summer.
LikeLike
Betsy qualifications? Demonstrated Incompetence
LikeLike
I would love to respond to the person who asked the question “how is Betsy not qualified?”. She has never taught in any type of school. She has no training at all in education. She doesn’t understand the workings of public education. She pushed for charter schools in Michigan. They failed.
LikeLike
Oh Wow! This was something else! Very,Very, Smart & could be real thing! Can’t wait till they handcuff Trump,march him right out of our WH– #StandUpForOurNFL!!
Vonia “Kaye:
LikeLike
Cool story. Except for the fact that Devos doesn’t own Spectrum. You literally had to completely fabricate a key fact of your dog shit pile of nonsense.
LikeLike
FYI: excerpt: “…Spectrum Health is run by current Secretary of Education Betsy Devos’ husband, a Michigan-based healthcare system that comprises 12 hospitals, 18 urgent care facilities, and 48 laboratory centers. Devos’ brother, private security firm Blackwater founder Erik Prince, has additionally come under scrutiny, in part for his alleged efforts to set up a backchannel of communication with Russian officials during a January 2017 meeting in Seychelles…”
https://www.snopes.com/news/2018/07/24/dubious-conspiracy-theory-links-putins-daughter-russia-trump-collusion/
LikeLiked by 1 person
Betsy DeVos served as the chair of the Mi GOP.
Richard DeVos ran and was defeated in his attempt to be Mi Gov.
Spectrums access to geographicdata voter registration and demographics as well as health data is thought to be the best in the state.
Medicare and medicaid information has long been accessable to those who have the will to access it.
The DeVos are either the greatest thing since fried ice cream or the scariest thing since the boogie man, depending on who you ask. That’s just for starter conversation.
Have not heard even a rumor of rational for a Russian bank to donate 5 Mill to Spectrum. However is not difficult to understand why Spectrum might send’data’ to Trump Tower.
LikeLiked by 1 person
And another facet of this: Blackrock is an institutional investor in Spectrum, also tied up with Russia, via another bank, VEB, also closely tied to Putin.
https://www.bloomberg.com/news/articles/2017-08-07/russian-bank-at-center-of-trump-storm-lures-blackrock-fidelity
LikeLiked by 1 person
I’m in for Democrats!! I like Rachel
Alot!
LikeLiked by 1 person
Thought the same.
LikeLike
I can just hear Putin & Putingarchs saying, “All your Trumps are belong to us.”
LikeLiked by 5 people
What I think gets lost in the analysis is what does the Kremlin actually do with the voter email addresses? They wouldn’t need them to troll Twitter. And they would be of no use with Facebook… UNLESS using those addresses to target FB ads to specific people.
When advertising on FB, you can upload email addresses, and FB then matches them to the appropriate UserID and shows your ads to that person.
If investigators really want to know if the Trump campaign was using stolen data, they should subpoena Facebook advertising records — then they can see exactly what data was used when targeting pro-Trump ads during the campaign, where the data came from, in what form it came (literally, the excel files containing the addresses), and who paid for the advertising.
An extremely easy way for Putin or ANYONE to support a political campaign on Facebook using unlimited funds is to simply buy advertising. You don’t even need bots.
LikeLiked by 7 people
And intel agencies KNOW that Russia sent social media posts to align with their goals..to disuade fence post HRC fans into voting for the Heinous one, or for BS. Or even Mcmullin
LikeLiked by 2 people
If this data were a list of registered democratic voters, then if could be used for large scale disenfranchisement, e.g. By sending out voter confirmation cards and removing voters who didn’t respond quickly, as was done in many areas.
LikeLiked by 4 people
And they still do it. After a terrorist attack they had their bots go to work so that FakeTerroristAttack was trending on twitter.
LikeLiked by 2 people
Or just to stay home and not vote at all.
LikeLiked by 1 person
Jill Stein actually, instead of McMullin. Jill is connected to Russia, too.
LikeLike
“Jill is connected to Russia”
What connection?
LikeLike
Since we know the Russians are in the hacking business, the email accounts of regular people could simply be another means to gain access to the contact lists of those folks whose email addresses they have, too. They could then bombard them with all sorts of things, whether it be a scam opportunity such as “You’ve won! Now click this link to collect your prize.” Or something like, “We’ve detected a virus on your computer, click here immediately!” If someone bites, they are in and controlling that computer. Let your imagination run wild with the options there.
LikeLiked by 3 people
And now WH is asking for voter information which has all of the makings of cyber ID’s. mothers maiden, last 4 of SS, etc.
LikeLike
“If someone bites, they are in and controlling that computer.”
Actually, following a link does not allow anyone to “control the computer”, but nice try.
LikeLike
simple-touriste: While following a link doesn’t necessarily automatically infect every computer that bites, that’s mostly because most people have some kind of malware protection installed, either as a separate utility, or part of their computer’s operating system, or they’re using a browser, like Chrome, that refers to a blacklist and warns users that they may be infected if they proceed. But there are plenty of people whose computers aren’t secure, for which following a link to a malicious web page can indeed automatically inject malware that can do whatever the malware was programmed to do. If there are no barriers on the computer that just bit, and if the malware has been written cleverly enough, it can steal data and indeed “take control”, at least in the sense of becoming a bot computer for whoever distributed the malware. If none of this were true, then there wouldn’t be any malware like this, but there obviously is.
LikeLike
By what magic could a random link infect a computer?
LikeLike
“that’s mostly because most people have some kind of malware protection installed”
You do NOT make sense.
Without any “protection”, just opening a webpage does not normally “inject malware”.
And malware “injection” is NOT a thing. It is NOT a computer concept.
LikeLike
Didn’t Kushner play “moneyball” with the campaign? Strategically targeted areas in states that could go red if you can convince voters. Then you have DNC voter information, rolls, etc. and enough misinformation to sway people through targeted attacks to question what is real in regards to the candidate of their party.
LikeLiked by 4 people
It told them what precincts voting machines to hack in the swing states. Check out what’s happening in WI with OVER VOTES. (More votes than registered voters.)
LikeLiked by 3 people
WI, that is where the 3 to 5 million Illegal Aliens that rape everyone voted for Hillary!!!!!
LikeLike
In today’s modern technology, if you have older voting systems, it should be fairly easy to hack. WI and all those special elections were not won fairly. There was vote tampering. Once Russia had all Democratic voters information they would know whose votes they had to manipulate. Then on voting day they would sync people voting with a Republican vote instead of a Democratic vote. Please note: More people are beginning to see that Trump has a strategic agenda to cry voter fraud, fake media, etc… which keeps us busy so that the nefarious plans can be implemented. We are not dealing with a forgetful 70 year old man. We are dealing with a skilled con-artist that has never taken the fall for anything. Every politician or staff in the White House or Congress have skeletons in their closet. Trump used the rebelation of Russia’s hacking as a means to intimidate all politicians. His message is, if Russia can hack into the DNC, it can also find the bones in your closet.
LikeLiked by 1 person
I remember how hot to trot Trump and campaign were to hit those 3 states all of a sudden like.Now its apparent. Amazing.They dont seem to have a worry in the world. Thinking they can outsmart with fake news bots and troll proaganda….Come on GOV get it together 😱😈😨🤢
LikeLiked by 1 person
“Then on voting day they would sync people voting with a Republican vote instead of a Democratic vote.”
OK that made no sense.
LikeLike
what do you mean…”You” told them????
LikeLike
“IT” not “I.” “It told them what….”
LikeLike
https://www.washingtonpost.com/politics/the-mystery-behind-a-flynn-associates-quiet-work-for-the-trump-campaign/2017/05/04/fc86980e-3044-11e7-9534-00e4656c22aa_story.html?utm_term=.4f3a43bc891a.
Jon Iadonisi, a friend and business associate of former national security adviser Michael Flynn, had two under-the-radar projects underway in the fall of 2016.
One of his companies was helping Flynn with an investigative effort for an ally of the Turkish government — details of which Flynn revealed only after he was forced to step down from his White House post.
At the same time, Iadonisi was also doing work for the Trump campaign, although his role was not publicly reported, according to people familiar with his involvement.
The project Iadonisi was engaged in for Trump’s campaign focused on social media, according to a person with knowledge of the arrangement. What that work consisted of — and why his company was not disclosed as a vendor in campaign finance reports — remains a mystery.
LikeLiked by 3 people
Likely he was researching just how outrageously stupid a story they could pass on to certain voters. Witness Pizzagate.
LikeLiked by 1 person
So people really play dominos on cheese?
LikeLike
it is being kicked around that the russians attacked the voter rolls of states, did voter purge or changed registration on Dems so voila no vote for you Dem Dog. Feasible and no direct attack at election system.
LikeLiked by 3 people
Send this to Tea Pain please
LikeLike
Are you an operative within the Facebook ad sales department?
LikeLike
Jared did exactly this, legally, to improve the sale of Trump gear over Facebook. Used data from Cambridge Analytica. Improved sales 10x.
LikeLike
Zzzzzzz. . .
LikeLike
It’s September 9, and I just read your post. We now know that Russia did buy ads on Facebook. Perhaps you should be working for Robert Mueller!
LikeLiked by 1 person
Now 5 months later your comment is amazingly accurate!
LikeLike
Kushner Cambridge Analytica Seychelles Prince De Vos Bingo
LikeLike
And we are up to date. Facebook CEO testifies to Russian ad buys…
LikeLike
Fake public comments on federal rule-making, using the identities of real people, for one thing. Millions of fake comments, originating in Russia, always in support of whatever idiocy Trump and his goon squad are attempting.
LikeLike
Comments are comments. They cannot be “fake”.
LikeLike
LikeLike
Jared bragged he had 14 million emails and CREDIT CARD NUMBERS of trump supporters.
LikeLike
That would most likely be gathered from his small donor contribution payments.
LikeLike
Seriously? OMG…He’s the spitting image of his father-in-law…sigh. But of course, the same lying, entitled, idiot who thinks he’s playing w/ cards instead of people’s lives around the world. Thinking of KARMA and knowing it will be fast and furious on the unconscious.
LikeLiked by 2 people
NIGHTMARE. And, his dad was tryin’ to get the the rest of the info from voter registration. Hats off to the states that said a ReSOUNDING “NO!!!!” No dicktatorship for us. No one is above the law even ‘weeeee-zils.’ Karma is faster and swifter: my consolation today. And, knowing Mueller is in charge of bringin’ the TRUTH to light.
LikeLike
Even the Republican state governors said No Way Jose.
LikeLike
Awesome work Tea Pain! I became aware of certain propaganda campaigns, and then became horrified to see a front running presidential candidate delivering it, then even more horrified when he became president. I am praying that he will be successfully stopped, and greatly appreciate your work towards that end. Many thanks!
LikeLiked by 5 people
In here by researching all-things-Trump on May 20 2017, I realize that Jared is the ‘killer’ mind behind the whole thing, no wonder Trump loves him – altho right now he may be getting push-back from Trump becos of all the investigatin’ going on ! BUT it has me wondering if FBI etc will discover now that yes – ‘collusion’ was going on to get Trump elected via all the methods described here, but no actual crime was committed – in other words it is all a huge complicated set of Russian assisted machinations for whatever advantage there could be to them – but there will be nobody going to jail in the end because it was all an exercise in data marketing – Super Duper & really envied now by Democrats – but is this a crime ?????
LikeLiked by 1 person
Yes, if this is indeed what happened, it is collusion. And collusion with a foreign government to affect an American election is treasonous.
LikeLiked by 5 people
As they say, “Follow the money.” And data connections now too!
LikeLiked by 3 people
I would see it as a crime any time that an American citizen, especially one so close to the president, works to further common goals with a known enemy, and all the more when there is strenuous effort at secrecy. That is the very definition of ‘espionage’! I wouldn’t have wanted my personal information provided to them, nor do I want it provided to Trump now! There has been no valid explanation as to why he wanted it or what would be done with it. But in light of what’s in this article, since Trump is already looking forward to the 2020 election, it’s entirely plausible that he wants us to hand over the very information that would rig the next election in his favor.
LikeLiked by 1 person
Not if one is a Repugnant. Nor if one is hangin’ by a thread of denial. Is that the real question? These ‘kids’ lives need to change: look who they have to look up to….that’s what I find criminal. Worst Parent Award vs. Give me Obama as a Dad any Day! @POTUS44
LikeLike
that’s a good question, but it would be considered a crime because a campaign cannot legally receive something of value from another country and there is no question that services like online marketing (ads), data (hacked or otherwise) and/or data intelligence have tremendous value. As does opposition research like what was offered to Trump Jr that he was so excited about. All of those things have value and therefore are illegal for a campaign to receive; so if these things are proven to be true then there likely won’t be a collusion happened but no crime was committed situation.
LikeLike
Has it been est as false that a Russian bank “donated” 5 million to Spectrum Health in MI ; that there were multiple data exchanges betwn Russia, Trump Towers/Mar Lago/Spectrum.? Was that merely rumor because of the DeVos /Prince connection to Spectrum and their access to mi voter inf due to prior State elections?
LikeLike
“All of those things have value and therefore are illegal for a campaign to receive”
Nope. You made that up. That’s fascist BS.
LikeLike
“works to further common goals with a known enemy”
like Iran?
LikeLike
I will believe all of this if & only if a neutral body is formed to analyze this mess & normalize our poor manipulated world politics !!
Many , must be imprisoned; many must be charged With treason… & euthanized !!
LikeLiked by 3 people
Many are guilty of treason then: Comey, Mueller, Hillary, Obama
LikeLike
Tea Pain, you are a genius! I hope this moves the investigations along in a timely manner. I don’t think our country can take much more. Already it is going to take us a long while to recover from what has happened to the US up to this point. I realize there are many pieces to the puzzle, but it seems as if there is more to the puzzle each day. Trump is a dangerous man, and he should not be in the WH. I truly believe this. Those around him must know it, so what is it that keeps them quiet? Food for thought. You are an interesting man. Thanks–Marilyn
LikeLiked by 4 people
Tal como acusação comiseração acordo assumido no aliança, Função da Resistência isto em cima
de era de estabelecimento compadecimento Programa Intestino a Suplementação
com Ferrete perante a humanidade os municípios, cujo propósito é
acionar a suplementação absoluto desde crias com 6 a 18
meses, gestantes por meio da 20ª semana e também mulheres no pós-parto. http://Postcards.shibbs.co.uk/mboard/msg/4538.html
LikeLike
Los consumidores finales necesitan una solución completa. https://usados.pplware.sapo.pt/author/emiliebisbe/
LikeLike
If Spectrums health care data was used outside of a medical environment then each use is a HIPPA violation. That’s big trouble for everyone involved. String ’em all up.
LikeLiked by 4 people
That’s true and the HIPAA law prescribes a fine of $4k per violation, if proven for millions of Michigan voters this translates to billions in fines to Spectrum – easily enough to bankrupt the DeVos family!
LikeLiked by 3 people
YES HIPPA COMES INTO PLAY
LikeLike
TeaPain, great stuff, but I have a question regarding Cambridge Anal. All of the data including emails, CC info, personal data that is being shared could have been purchased legally through dozens of US data companies. I was in this business of marketing and I know I can buy all of this. So Trump Campaign and CA can claim they purchased or acquired all of this legally. My question is how can it be proven that “hacked data” entered the system? I have a theory that CA is the “front end” and legitimate business entity to a military grade targeting campaign. They appear to be doing legal, if not creepy, next gen social media marketing, but the secret sauce is they are a front to a much more sophisticated and illegal endeavor used by Flynn, Gorka and other Intel individuals at the campaign w the Russians.
LikeLiked by 2 people
This is how it was done, with Russian propaganda (fake news). http://www.youtube.com/watch?v=n8Dd5aVXLCc
LikeLiked by 1 person
White collar Orwell.
LikeLike
My honest opinion is, the reason they stole the voter rolls is to hack the votes. Why else? If they just wanted to troll on social networks, they didn’t need to hack voter rolls for that. Check out unhackthevote.com … they’ve figured out a lot of shady going on with voting machines. For example, the total of votes in certain precincts in WI have over 100% turn out for registered voters. How the hell does that happen? And coincidentally, these precincts lack paper ballot backups in order to audit votes…
LikeLiked by 2 people
Unconnected machines require physical access, which would be extremely difficult to do—though not impossible, and only necessary to do in a few key locations. Fiddling with the actual registers of voters might be a bit easier.
LikeLike
Online Marketing costs money and anyone in that business will tell you it’s all about the Return On Investment. So if you can target certain voters in swing precincts in swing states then you can get a great return on your investment! Target enough Bernie voters in PA, MI and WI with negative Hillary “news” and content on Facebook to keep them from turning out to the polls or even switch to Trump and you’ve got yourself the White House!
LikeLiked by 1 person
“negative Hillary “news””
What kind of “news” about Crooked Hillary could make any difference?
LikeLike
How would voter roll allow vote hacking?
“For example, the total of votes in certain precincts in WI have over 100% turn out for registered voters”
Are these Dem managed?
LikeLike
One thing has been bugging the hell out of me (actually, thousands of things but I’ll keep it short) How is the stealing of names, emails and addresses by Spectrum Health not a violation of HIPAA??? This is part of protected medical info.
LikeLiked by 3 people
I think it would have to be linked to a piece of health care info to be a HIPAA violation.
LikeLike
Not necessarily. Colluding with Russia to steal an election is treason, so I don’t believe they were concerned about pesky HIPAA violations. However; maybe that could be the driver to access the details of these transactions–investigating possible HIPAA violations.
LikeLiked by 2 people
Having worked on several healthcare systems, and on fixing problems from several HIPAA data breaches… It is considered to be a HIPAA violation if you disclose that someone is insured, or if that insurer shares personal data, which includes address and phone number, without the person specifically releasing it. SS# is also protected. (There are far less risky ways to get all that information that wouldn’t be a HIPAA violation, but I think this is probably a case of billionaires saving money by using data they already have, confident it’ll never get out.) I had a health insurer client who got massive fines and the data that was lost: names, addresses, phone numbers, SS#.
LikeLiked by 1 person
What would that “collusion” be?
Why would Russia help Donald Trump?
LikeLike
we’re not dealing with people who are concerned with ethics here.
LikeLike
Reblogged this on Macjoyful's Minimal Musings and commented:
Money and Data Laundering Help Steal An Election
LikeLiked by 1 person
I work for a technology company and am very familiar with replication. You explained it perfectly and pointed out the ease at which replication is completed. This would appear to be the smoking gun. What’s next???
LikeLiked by 4 people
Reblogged this on Coloring Outside the Lines and commented:
There’s fingerprints. Wonder if there’s a trail anywhere….
LikeLike
Where does Pascale fit into this network.
LikeLike
I think Parscale set it up. It wasn’t Kushner, who is just the broad-brush type of guy.
LikeLike
Retired and burned out IT engineer and QA mgr here, among other things. Good work, Tea Pain. Stay away from the bad guys and be sure this good stuff ends up in good hands. Power to the little people! #Resist
LikeLiked by 2 people
TEA PAIN: I passed your article and information on to my Senator Claire McCaskill (D-MO), hoping it would be forwarded to the Mueller and the Senate investigations. Of particular concern, in my opinion, is the SPECTRUM HEALTH involvement due to the fact that the right-wing DEVOS family owns it, and Betsy DeVos is sister to ERIK PRINCE, who created the BLACKWATER mercenaries for hire (now part of Prince Group) used as no-bid civilian contractors by the lawless Bush/Cheney administration in Iraq (where they murdered civilians) and Afghanistan. Was the Trump appointment of an unqualified (anti-public education) DeVos the QUID PRO QUO from Trump for helping with the DATABASE REPLICATION? This should all be passed on to the “Suspicious Activity” division of Homeland Security, but should also be made public on “The Rachel Maddow Show” of MSNBC so that the Russia-colluding Trump people cannot cover it up. FELIX SATER, a long-time Trump business partner, is the Russian-born son of the Russian MAFIA crime boss with offices in Trump Tower two floors below Trump’s, so it would be good to know if the Russian MAFIA had a hand in this three-server activity.
LikeLike
I was pleased when the question as to FBI knowlege of the data exchange and parties involved received the response FBI had the information and more.
LikeLike
there was a raid on Trump Tower ages ago. FBI got the servers. And the SIGINT. oh yeah.
LikeLike
“Anti public education” is not “unqualified”.
Public education and control of the minds by state propaganda is a fascistic proposition.
LikeLike
Fake news. The server was not a Trump server and was set up by McMullin with the name “Trump Orgainzation”. Anyone can see this if they actually did research on the server. Instead, people want to lie.
LikeLike
LOL
LikeLike
Tea Pain, how do you believe this fits in with Robert Mercer an the Cambridge Analytics gang?
LikeLike
Really interesting and it will get more interesting when FBI and other US security find additional data maybe including data between Alfa and Kremlin
LikeLike
Can you tell us about the time-of-day field in the server logs? UTC? Local to each ClientIP? To mail1.trump-email.com (any idea about location?)
Many thanks for your efforts!
David S
Vancouver WA
LikeLike
I’m struck by the last piece
“Trump/Spectrum operatives and employees in the United States could interact with this list and have no clue the origins of the data were nefarious. This plain-sight approach was the key to its success.”
Especially “have no clue the origins of the data were nefarious” ie: plausible deniability or “no collusion” It appears to me that statement if, if accurate is why Mueller found no conspiracy, yet could not exonerate the President. My summary follows with a football quote:
“Winning isn’t everything, it’s the only thing.”
LikeLike
You must love science to do well in this program. Admission is competitive. A typical GPA for a dental hygiene student is about 3.7. Only 12 spots are available.
Portuguese water dog cost
LikeLike
It is very helpful information.
Please keep it up, from your marvelous thinking.
Regards by:Top Website development company, Lahore, Pakistan “Bit links tech”.
LikeLike
Great investigation… If only someone had captured the contents of these transmissions… Probably a database backup somewhere… If only that got leaked…
LikeLike